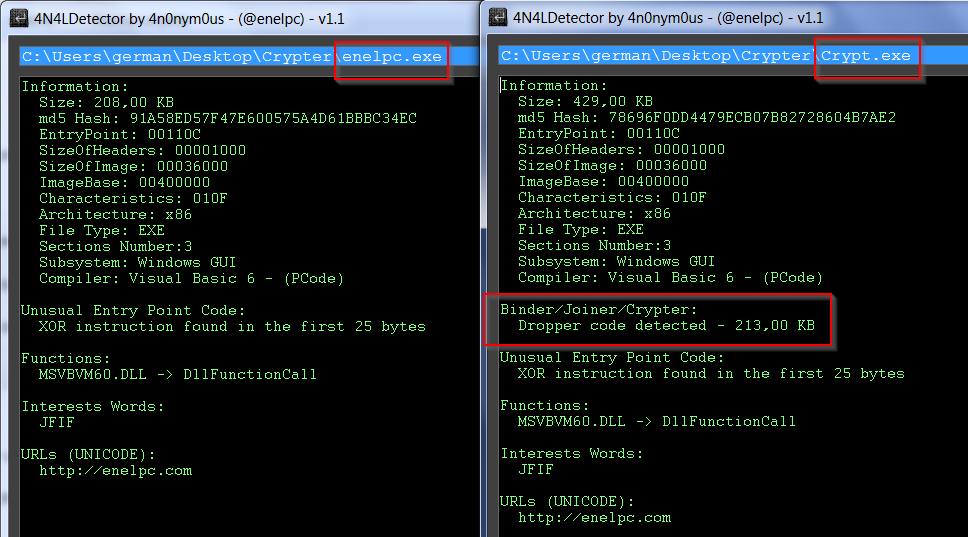
4n4lDetector v1.1
Fuck what fucking time ago out there! Now it is the awkward moment when everyone is back to haunt you. If you get into bed and I enfold, raisins heat. If you poke a foot by the end of the sheet, you run the risk of losing the little freeze. If you come out on long pants, even gayumbos merge with the cheeks of your buttocks, and this with perspiration your balls become number one public enemy. Why you the start to sweat all! And if Instead decide to spend the shorts ... date by fucked because something bad has to happen to you, you listen to me ... this is a no live! The truth is that I do not want to write the post jajajaa pffffffff ... rather be thrown into the little sun on my terrace sucking flash pole , but as alternatives after a weekend so I was only movidito post something or enter Putalocura , and I know what will be happening, but lately not updated with good content, for that ... I'm losing interest. So I said ... I will give them to the kids and especially the